Hello everyone
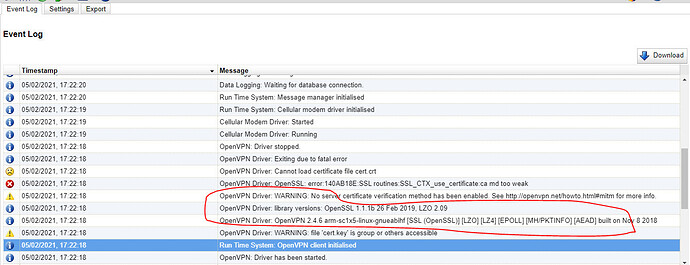
My SG Gateway occur this problem when connect to VPN Server, the VPN Server only create MD5 type
Do you have any idea about this case? Image is below
I think the errors above ones circled might be the reason for the subsequent error messages. It looks like you are not providing it any certificates to use. I think this documentation on the openVPN site might help
Setting up your own Certificate Authority (CA) | OpenVPN
Hi Deryck
Does SG Gateway accept certificate in MD5 type or just SHA?
I have not been able to find any info saying MD5 is supported. I did find this info on md5 regarding openVPN.
Hi Deryck
Also, can a SG Gateway connect to 2 different network field? Like 192.x.x.x and 172.x.x.x
If itself cannot, do you have any recommended solution with hms devices?
Hi @PhiNguyen , I found a little more on setting up openVPN.
Reference manual for OpenVPN 2.4 | OpenVPN
To some extent some versions can connect to two netoworks. Devices with a Ethernet based fieldbus option such as EIP and Profinet have a second interface that can be configured for a second subnet.
Deryck
Thank you alot Deryck
Is there any possible way to use MD5 on SG Gateway? like downgrade the OpenVPN driver for example
Can you provide me with the exact model/order code of SG gateway you are using?
Deryck
Thanks, I am checking with the Ixxat team on this. I am doubtful this will be possible since the device was build after MD5 was fully depreciated.
Discussing this with my colleagues they confirmed that MD5 is not allowed anymore. We are using 2.4.8, this looks to still have support based on the change logs. It looks like there might be a workaround by setting tls-cipher=DEFAULT:@SECLEVEL=0.
Latest version 2.4.5 does not connect with VPN servers · Issue #229 · OpenVPN/openvpn-gui · GitHub “SECLEVEL=0 is only a temporary quick fix – do not use it as a long-term solution” It would be best to generate new certificates with SHA-256 see {Resolved} openssl new versions consider md certificates too weak - OpenVPN Support Forum
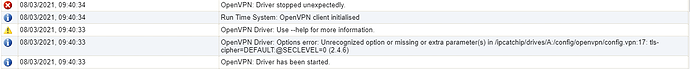
Deryck
Hi Deryck, thank you and your team for your respond
But, is that line make OpenVPN run without certificate or security algorithm?
Also it turns out like this:
It is my understanding that this would allow it to use MD5. It looks like is is disabling TLS.
Can you copy and past the configuration string you are using?
Again, MD5 is not secure and not too far from using no security. If you want to use a secure connection I recommend updating your VPN server to support TLS with SHA certificates.
Deryck
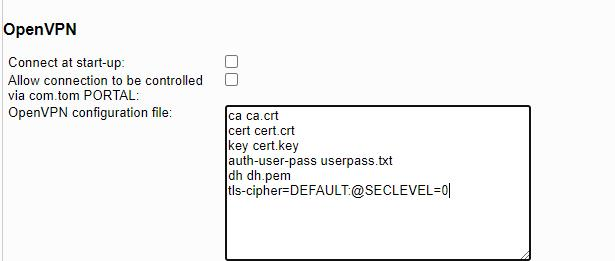
This is the configuration file from my server
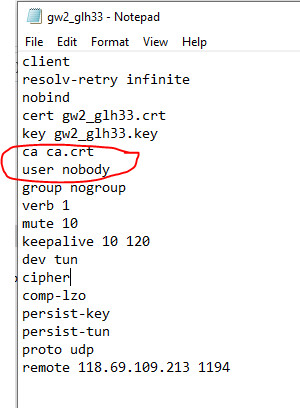
This is the configuration file i used in SG gateway
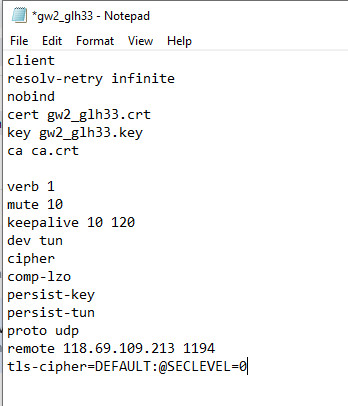
Thank you for your replying
client
resolv-retry infinite
nobind
cert gw2_glh33.crt
key gw2_glh33.key
ca ca.crt
verb 1
mute 10
keepalive 10 120
dev tun
cipher
comp-lzo
persist-key
persist-tun
proto udp
remote 118.69.109.213 1194
tls-cipher=DEFAULT:@SECLEVEL=0
Hi @PhiNguyen ,
This might be an issue with having cipher twice. You could try the following format to see if it helps. tls-cipher "DEFAULT:@SECLEVEL=0"
or simply DEFAULT:@SECLEVEL=0
The open VPN version we use might not support this.
Deryck
Discussing this with a colleague he believes TLS 1.3 might not* allow the cipher. Checking with the product manager we are not able to revert to an older version.
Deryck
Thanks for your enthusiastic support, Deryck